 "ttyymmnn" (ttyymmnn)
"ttyymmnn" (ttyymmnn)
02/13/2019 at 10:45 ē Filed to: None
 0
0
 30
30
 "ttyymmnn" (ttyymmnn)
"ttyymmnn" (ttyymmnn)
02/13/2019 at 10:45 ē Filed to: None |  0 0
|  30 30 |
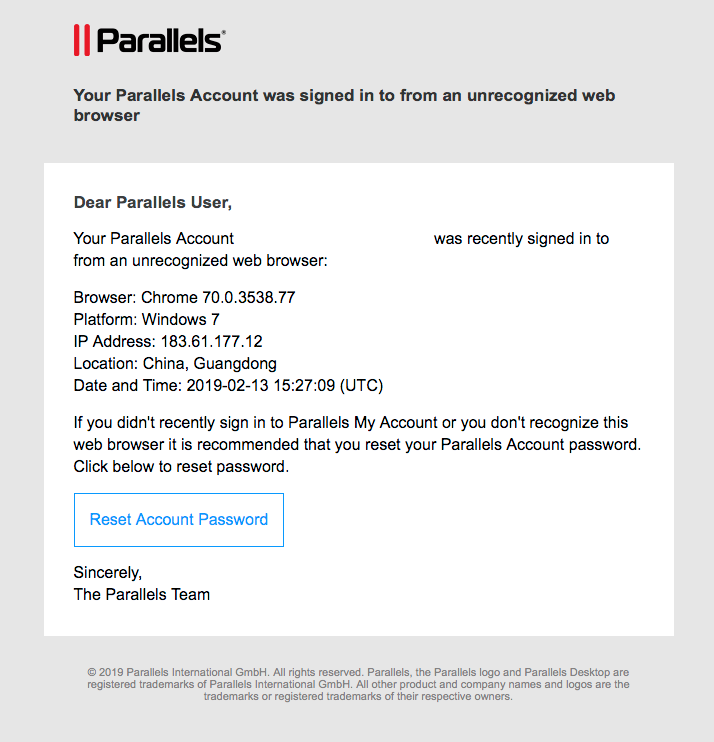
Just got two emails from these people saying somebody logged into my account using one of
my email addresses
, one from China the other from Brazil. Parallels is a Windows emulation software for Mac, and I havenít used it in YEARS. I know this particular email @ is out there because I recently saw a significant uptick in spam to this account. My sense is that I should just ignore this, as the email itself might be a scam. Thoughts?
 KingT- 60% of the time, it works every time
> ttyymmnn
KingT- 60% of the time, it works every time
> ttyymmnn
02/13/2019 at 10:51 |
|
Easy fix

 WiscoProud
> ttyymmnn
WiscoProud
> ttyymmnn
02/13/2019 at 10:51 |
|
At minimum change the password. If you havenít used it in years, i would just delete it.†
 ttyymmnn
> WiscoProud
ttyymmnn
> WiscoProud
02/13/2019 at 10:52 |
|
I donít even know what the password would or could be. Like I said, I havenít used Parallels in probably 10 years.
 The Ghost of Oppo
> ttyymmnn
The Ghost of Oppo
> ttyymmnn
02/13/2019 at 10:54 |
|
First make sure these emails arenít phish.† What is the email address that sent them to you?†
 Party-vi
> ttyymmnn
Party-vi
> ttyymmnn
02/13/2019 at 10:54 |
|
I bet that link will ask you for your old password to reset it, and then BAM! They got ya.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 10:54 |
|
Easy enough to go Parallels yourself and change/reset your password. That avoids any issue with it being a scam (i.e. go here instead of clicking the emailís link: https://my.parallels.com/login ) .
In theory though, it shouldnít matter unless:
You use that same password elsewhere (in which case you should change anywhere else you use it as well)
You have a credit card tied to the Parallels account that could be used to purchase software from them.
 ttyymmnn
> The Ghost of Oppo
ttyymmnn
> The Ghost of Oppo
02/13/2019 at 10:55 |
|
noreply@parallels.com
 ttyymmnn
> Party-vi
ttyymmnn
> Party-vi
02/13/2019 at 10:55 |
|
It did, but I donít even know what it is, and Iím not going to try guessing.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 10:56 |
|
Then you can just use the forgot password link, since itís obviously still tied to your email.
 ttyymmnn
> facw
ttyymmnn
> facw
02/13/2019 at 10:57 |
|
1. I have no idea what the password is, so I donít know if I use it elsewhere.
2. I have no idea if they have my CC.
I suppose I could try to log in with some guesses of the PW and see that happens.
 facw
> The Ghost of Oppo
facw
> The Ghost of Oppo
02/13/2019 at 10:58 |
|
You should never rely on the sender being accurate, thatís easy to spoof (thereís a push for better sender authentication, but we definitely arenít there yet).
 facw
> Party-vi
facw
> Party-vi
02/13/2019 at 11:00 |
|
The email is way more polished than Iíd expect from a scam, though itís possible they cloned a real one.
Regardless, blindly clicking links in emails, especially for something like this is definitely not a good idea. Better to visit the site directly.
 ttyymmnn
> facw
ttyymmnn
> facw
02/13/2019 at 11:05 |
|
I did this, and am going through the process of deleting the account. It doesnít look like there is anything to steal anyway.
 deekster_caddy
> ttyymmnn
deekster_caddy
> ttyymmnn
02/13/2019 at 11:07 |
|
Either way, it means somebody may have hacked their way into your account. Let Parallels know about it, there may be a data breach afoot. The other option, of course, is that this is strictly a phishing attempt and the link is bogus. Do not use the link in their email.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 11:09 |
|
So 2 says definitely change your password there.
For 1, you can copy the URL from the email and see what it is (beware, scammers may try to disguise this, but if you paste it into a browser URL bar, the real domain should be in black vs. gray. I wouldnít actually load the page though). You could also contact Parallels support and ask them to confirm they sent the emails. Regardless, if it looks at all possible the email is legitimate I would change all your passwords (especially for email/banking/investment accounts). This is critical if you make a habit of reusing passwords between sites. Itís a pain, but youíd rather not find out the hard way that your password had been compromised.
 ttyymmnn
> deekster_caddy
ttyymmnn
> deekster_caddy
02/13/2019 at 11:09 |
|
Well, I assume Parallels knows since they sent me an email, albeit automatically. I have gone through the actual site (not from the link) and am deleting the account. I havenít used it in probably 10 years, and it doesnít look like there is anything sensitive there anyway.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 11:11 |
|
You can also try your email at https://haveibeenpwned.com/ †or other similar sites (donít enter your password anywhere though). The results can be a bit scary though.
 ttyymmnn
> facw
ttyymmnn
> facw
02/13/2019 at 11:15 |
|
I know for a fact that this email has been pwned. We recently went though and updated/changed passwords and enabled 2FA wherever possible on critical accounts. I have been wondering if I should start using some sort of password aggregator.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 11:17 |
|
Using some sort of password vault is a good thing. I worry about having everything contained in one place, but I think the benefit of using strong passwords outweighs the risk, especially when combined with 2-factor.
 ttyymmnn
> facw
ttyymmnn
> facw
02/13/2019 at 11:26 |
|
Does a PW vault generate unique passwords, or does it just remember all the PWs you tell it? As it is, we keep our logins and PWs on a PW-protected Word document. My 78-year-old dad keeps all of his on a piece of paper next to his computer....
 random001
> ttyymmnn
random001
> ttyymmnn
02/13/2019 at 11:32 |
|
Personally, I'd panic.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 11:34 |
|
Most vaults will include a generator, so you can get a strong password on the fly. I use KeePass (which is not the easiest solution for mobile) and it gives me this when I create or change an entry (it actually generated one automatically when you create something):
These options generated this, which is not going to be easy to crack:
DZ5#*.C@ND5F9NT*!Gíp
Pain to type, but since you have it in the Vault you can just copy/paste, except in stupid programs that donít let you paste into password fields (non-standard behavior), though vaults usually come with some alternate method for filling those.
 deekster_caddy
> ttyymmnn
deekster_caddy
> ttyymmnn
02/13/2019 at 11:35 |
|
Emails can be very easily spoofed. I could craft an email from just about anywhere and make it look like this. Thatís why you donít use the link directly in the email - it can easily be a total fake. Anyone can fake almost any Ďfromí address in an email and make it look legit. Thatís the other side of this concern - the email could be from a hacker asking you to click the link to their fake website that looks a whole lot like the real site, and when you try to log in what you end up doing is giving them your login credentials...
alternatively someone genuinely hacked into your parallels account, which means your password got picked up somewhere else in some other data breach (not necessarily from parallels but it could be ) and hackers are now using your old passwords to try logging in various places. If Parallels was aware of a data breach with their accounts they should be taking other measures, one being alerting all of their users to the breach - this hasnít happened that Iím aware of, the Mac user community would be all abuzz about it.
 ttyymmnn
> random001
ttyymmnn
> random001
02/13/2019 at 11:36 |
|

 ttyymmnn
> facw
ttyymmnn
> facw
02/13/2019 at 11:38 |
|
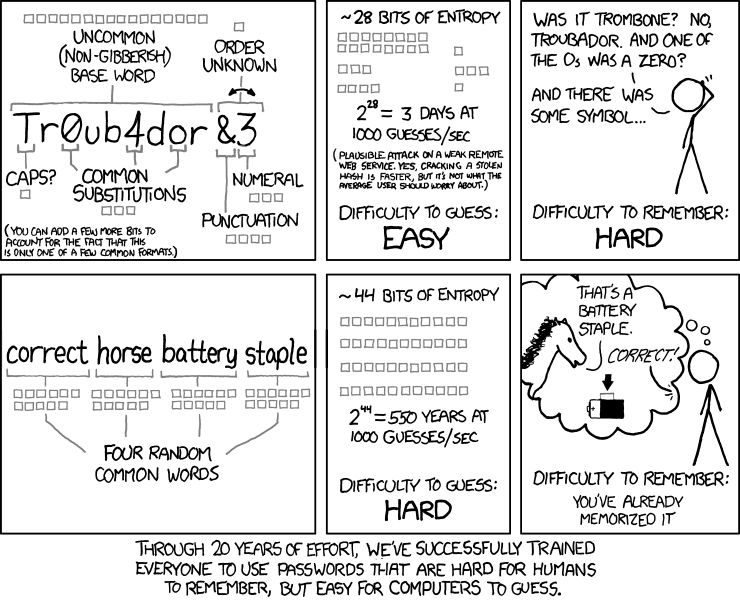
Nifty password, but what about this:
 ttyymmnn
> deekster_caddy
ttyymmnn
> deekster_caddy
02/13/2019 at 11:40 |
|
Iím going through my list of passwords and finding those that use this email as a login. Then Iím changing the passwords. Probably a day late and a dollar short, but better to do it than not. I donít think there are that many sites with this email as a login, and my critical banking sites have recently been updated with new passwords.
 facw
> ttyymmnn
facw
> ttyymmnn
02/13/2019 at 11:47 |
|
Iíve read mixed things about this approach. A correcthorsebatterystaple password is certainly much stronger than most passwords people use, but the fact it relies on dictionary worlds makes it a lot more crackable than xkcd says. Itís essentially only four letters (from a very large alphabet).
Obviously the move to two factor is the real win here (though SMS -based two factor is starting to show vulnerabilities given that we donít do a good job securing and authenticating on our phone network).
 You can tell a Finn but you can't tell him much
> ttyymmnn
You can tell a Finn but you can't tell him much
> ttyymmnn
02/13/2019 at 12:00 |
|
That email may not actually be from parallels. Never assume an email is from the sender that it appears to be, and never click on links or open attachments in emails unless you are expecting them from someone you know.
If an email is from someone you know, you still need to be suspicious if the attachment or link isnít something you were expecting. Always verify through a second independent method of communication if something in an email looks suspect.
 deekster_caddy
> facw
deekster_caddy
> facw
02/13/2019 at 20:18 |
|
The xkdc comic is one of my favorites. A system trying various combinations of dictionary words might do worse than one trying random character combinations. There is no way to tell how many characters to use, therefore how many word combinations to use... so any brute force attempt will fail with the correcthorsebatterystaple method. More math than I care to do, but itís probably on par with a 16 character randomly generated password, and thatís only if you know that itís all words with no numbers or symbols... throw a symbol into that mix at some point that makes sense to you and itís pretty bulletproof - as far as brute force attempts go. The issue with password hacks is they will find some other way to get in before brute forcing an 8 character password. Some kind of social attack or theft of the encryption key will get them there much faster.
At any rate, use a password managed and long randomly generated passwords. I like LastPass. Itís free now for mobile and desktop. They sync your database across devices, but they donít ever have your keys.
 facw
> deekster_caddy
facw
> deekster_caddy
02/13/2019 at 20:26 |
|
The other problem that you can run into with the chbs method is that a lot of sites choke on long passwords (that arenít even that long). This is their fault, and frankly worrying given that they should be immediately passing the password to some hashing function so length shouldnít matter. Regardless of fault itís common enough for sites to limit you to 20, and Iíve seen some instances of 16 or even 12 character limits, which is way too few for a secure password made only of dictionary words.